2 phase authentication
Securing your network from the outside world
How
1.A user logs into our secure website using their known username and password.
2.They request that a new “one time” password is generated and sent to their mobile phone via SMS.
3. They initiate a new VPN connection with their known username, a known 3 digit PIN, and the new “onetime password” as per the new SMS.
More detail…
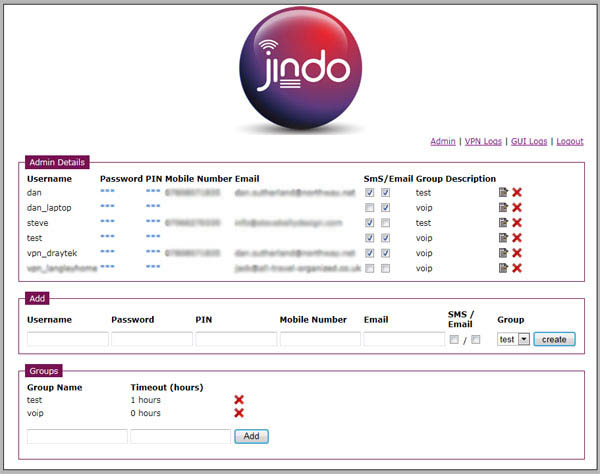
The system comes with an administrator account where all users are created and system logs can be viewed. Upon first login the system will prompt you to re-set the password.
Each user must have a username, password, 3 digit PIN and mobile number and be a member of a group. The purpose of a group is to define the validity period of their password.
Password expiry period
When a new one time password is generated by a user it is valid for 15 minutes. If the password is NOT used within 15 minutes (doesn’t successfully login) then it will expire and a new password will need to be generated.
If a user DOES log in within the first 15 minutes then the same password is valid for as long as specified in the group. Eg if a groups called “homeworkers” has a timeout of 3 hours. The password will be valid for 3 hours after the time of logging in.
User generates password at 12:00.
User Logs in at 12:05.
Password will be valid till 15:05.
This means that if a user logs out, or is logged out caused by outside factors such as a drop in a 3G broadband connection. They will not need to create a new password each time.
1. A user logs onto the website with their username and password as setup by the admin user.
2. A SMS containing a one time password is then sent to their defined mobile phone number.
3. The user logs into the network via VPN with their username and the password is their 3 digit PIN, plus the new one time password. Eg. PIN24hw6
Admin interface
The admin interface provides the following:
- 1.Creating/removing user accounts
- 2. Configuring a users:
- a. Username
- b. Password
- c. 3 digit PIN
- d. Mobile phone number
- e. Member of which group
- f. Description
- 3. Creating/removing groups
- 4. Amending the password timeout for a group
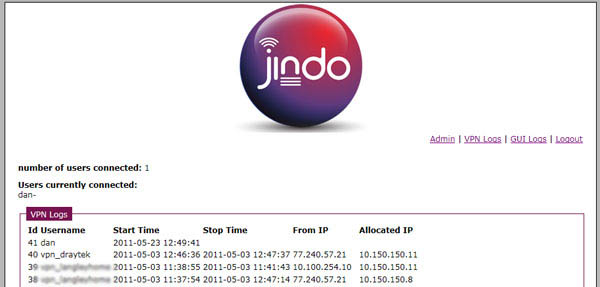
- 5. VPN logs to display
- a. Currently logged on users
- b. All login activity displaying, start time, stop time, from IP address and allocated IP address
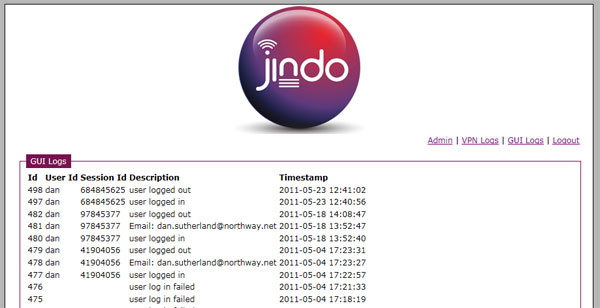
- 6. GUI logs to display:
- a. When a user logged in to the website
- b. When a SMS was sent
- c. When a user logged out of the website
The technology
Northway host a cluster of DELL servers in a virtualised environment. There are 3 parts to the service:
1. A front end server managing the login interface
2. The back end database and RADIUS server
3. The firewall or router that acts as the VPN end point. (Please see our list of support devices).
With parts 1 and 2 being hosted in Northway’s secure environment you can be sure that your data is secure. Northway can either provide you with a managed router or firewall. Or we can assist in configuring your existing equipment with our two phase authentication platform.